Unlocking Seamless Guest Experiences in the Hospitality Industry
In the age of digital transformation, the hospitality industry continues to evolve, offering more personalized and convenient services for their guests. Bluetooth Low Energy (BLE) technology plays a vital role in this evolution, providing an innovative and secure access control solution. In this article, we will explore how Sydney APX Apartments has successfully implemented BLE access control, revolutionizing the guest experience in their hotels.
The Power of BLE Access Control
BLE technology has numerous benefits for access control systems in the hospitality industry, including:
- Enhanced security: BLE provides strong encryption, ensuring that guest room access is secure.
- Seamless integration: BLE can be easily integrated with existing hotel management systems.
- Convenience: Guests can use their smartphones as digital keys, eliminating the need for physical key cards.
- Improved guest experience: BLE enables a more personalized and streamlined check-in process.
APX: A Case Study in BLE Access Control Implementation
APX, a leading hotel chain in Australia, has successfully harnessed the power of BLE technology to enhance guest experiences. Let’s delve into the key components of their cutting-edge access control solution.
State-of-the-Art BLE Locks
APX has installed advanced BLE locks in all of their guest rooms. These locks offer:
- High security: Incorporating the latest encryption standards, these locks protect against unauthorized access.
- Low energy consumption: The locks operate efficiently, reducing energy usage and costs.
- Easy maintenance: Firmware updates can be performed wirelessly, minimizing downtime.
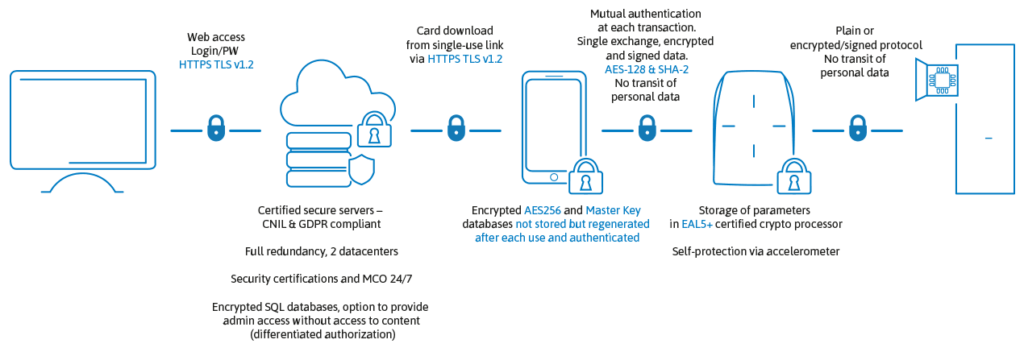
Seamless Integration with Hotel Management Systems
The BLE locks at APX are seamlessly integrated with the hotel’s management system, offering:
- Real-time data: The system provides real-time information on room occupancy and access events.
- Streamlined operations: Hotel staff can easily manage guest access, issue digital keys, and monitor security.
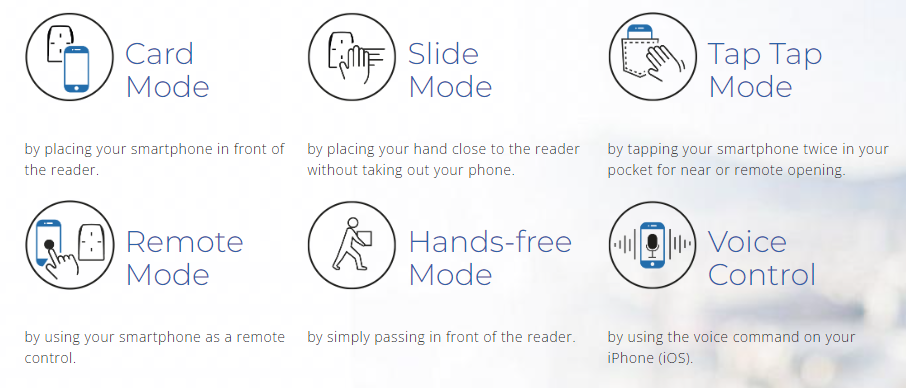
Smartphone App for Digital Keys
Guests at APX can download a dedicated smartphone app, which serves as a digital key for their room. This app offers:
- Easy access: Guests can unlock their rooms with a simple tap on their smartphones.
- Personalization: The app allows guests to customize their stay, such as controlling room temperature and lighting.
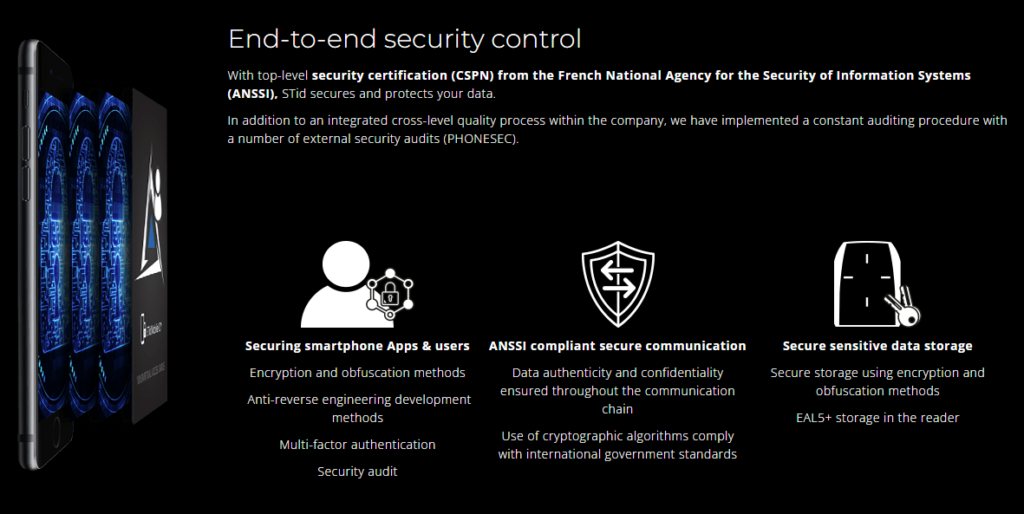
- Enhanced security: The app utilizes secure authentication methods to protect against unauthorized access.
The Impact of BLE Access Control on Guest Satisfaction
APX’s implementation of BLE access control has led to significant improvements in guest satisfaction, with benefits such as:
- Faster check-in: Guests can skip the front desk and head straight to their rooms.
- Enhanced convenience: The smartphone app allows guests to access their rooms easily and securely.
- Personalized experiences: The app provides tailored services, enhancing the overall guest experience.
Future Prospects for BLE Access Control in the Hospitality Industry
As the hospitality industry continues to embrace digital transformation, BLE access control is poised to become even more prevalent. Future developments in this technology may include:
- Expanded integration: BLE access control could be integrated with other hotel services, such as payment and booking systems.
- Increased automation: Machine learning and artificial intelligence could be utilized to further streamline operations and enhance security.
- Greater personalization: Advanced data analytics could enable hotels to offer even more personalized services based on guest preferences.
In conclusion, BLE access control is revolutionizing the hospitality industry, offering improved security, seamless integration, and enhanced guest experiences. As demonstrated by APX’s successful implementation, this innovative technology has the potential to transform the way